The path towards quantum communications
In a recent article, Boston Consulting Group (BCG) pose the question “Are you ready for quantum communications?”
If you’re new to the concept of quantum communications and quantum-safe communications, it’s well worth a read. It acknowledges the need for both governments and companies to move towards stronger cyber security, recognizing the threat to classical cryptography posed by the advent of the quantum computer. It outlines three core technologies that will be used to secure future network infrastructure, the main use cases, and the factors that will drive adoption on a global scale.
BCG gets straight to the point: the need for quantum communications is clear – and urgent. We know that current public key cryptography will be broken in less than a decade. In our exponentially connected world and an ever-increasing volume of data that must be secured, governments and companies simply can’t afford not to seize the revolutionary technologies that transform the way we communicate and transmit data. It also highlights the risk for government and enterprise companies to see hacked encrypted data stored now and decrypted later when powerful quantum computers are available.
The good thing is that:
- These technologies are not futuristic: they are available today.
- Both the public and the private sector are actively investing in quantum initiatives (the global quantum effort is estimated at $36B).
Quantum resilience
In response to the threat to classical cryptographic resilience, two technologies have emerged as mainstream alternatives for securing tomorrow’s network infrastructure. Post Quantum Cryptography, or PQC, is the name given to the next generation of cryptographic protocols that leverage complicated mathematics to defend against quantum attacks.
In the US, NIST has announced the first candidate algorithms that will be standardized, and it is expected that the first standards will be published in 2024. It is worth mentioning that the implementation of these algorithms is still facing issues at the moment which means the timeline for migration is likely to take more time than expected.
The second solution, known as quantum communications, relies on the fundamental principles of quantum physics to guarantee forward security. It includes Quantum Random Number Generation (QRNG) and Quantum Networks (including Quantum Key Distribution, or QKD), and is already being used to provide additional security to existing network infrastructure. In contrast to PQC, the main advantage of these technologies is their maturity. In addition, QKD is considered to be unconditionally secure, as it is based on the laws of quantum physics, which cannot be broken by any currently known method. PQC methods, on the other hand, are only considered to be computationally secure, and may be broken in the future as all computational security comes with an expiry date.
It is important to understand that PQC, QRNG, and QKD are all important components of quantum-safe cybersecurity and will work together to create end-to-end security.
Quantum technologies
Quantum random number generators are widely used as a source of unpredictable randomness in applications beyond cryptography. Sectors as diverse as finance, automotive, gaming, and telecommunications are already leveraging QRNG to strengthen security. IDQ’s own QRNG chips are already established as the go-to technology for mobile and IoT applications. Recently they have also been used to secure orbital satellite communications, proving their suitability for use in even the harshest of environments.
Quantum networks, also referred to as quantum internet in BCG’s article, are both mature and in their infancy as two specific use cases are mentioned: the secure transmission of data across private and public networks using quantum key distribution (QKD); and the interconnectivity of quantum computers.
The first use case is of course the most mature. QKD deployments are flourishing all over the world, notably in Europe through public initiatives, and in China which started building its own nationwide QKD network about a decade ago, identifying the technology as one its priority in their national strategy. On its side, ID Quantique has deployed QKD commercially since 2007. Since then, IDQ has deployed QKD networks and testbeds on all continents and has built one of the most sophisticated QKD network in South Korea, achieving unmatched scalability, usability, and interoperability.
The second use case represents the holy Grail of the quantum community’s vision: the quantum internet. This represents a completely new kind of network and requires advances in various quantum technologies such as computing, sensing, and communication. This vision is particularly exciting as, like it was the case for the “regular” internet, we can only envision a fraction of potentially unlimited applications.
Quantum technology adoption
BCG’s article summarizes the adoption of quantum communications technologies in three waves, which are guided by several factors, from government funding and mass-market devices adoption to the emergence of new or improved technologies.
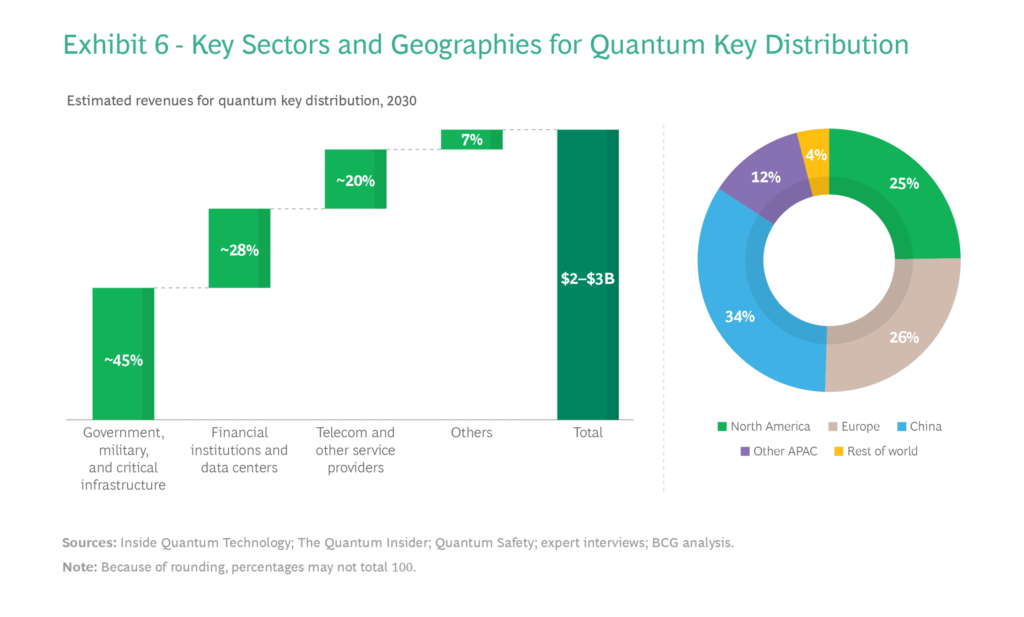
While financial institutions were among the early adopters of quantum technologies (quantum computing and quantum communications), it’s no surprise that the government and defense sector are probably the most advanced in terms of deployment, often counting with the support and expertise of telecommunication providers. For the latter ones, quantum-enhanced and quantum-safe communications represent much more than “just” unconditional security, but also a significant opportunity to develop new security-based services, opening up new revenue streams.
Get started with quantum communications
Bottomline, companies need to start preparing now. Quantum communications are a game-changer for today’s cybersecurity already and, as quantum computing technology advances and the risk of seeing stored data stolen and decrypted is higher every day, businesses failing to adopt quantum security will likely see their data confidentiality significantly compromised.
While it may seem like a daunting task, working with quantum communication providers to develop a quantum security strategy is the first simple step anyone can take today.



