With the digitalization and increased use of many critical services through our mobile devices, the use of quantum-enhanced security in our phones has proven to be a solution to count on. Simple and affordable to embed, easy to leverage, ultra-secure: QRNG creates opportunities and changes the game for phone manufacturers, telecom operators, app developers and end-users.
Increased mobile phone security through quantum technology. Today’s digital activities – from mobile banking and online purchases to messages over social media and work emails – have turned mobile phones into a goldmine of financial, health, business and personal information, raising the need for security to the edge.
Applications require the collection and transmission of a large amount of sensitive information including digital identification and use phone security algorithms to generate keys to encrypt client’s data securely.
Transmissions and data are protected by cryptographic algorithms using random numbers for encryption, digital signing, and hashing – the basic cryptographic implementations that protect everything digital.

QRNG offers strengthened security to mobile phone users
If the recent years have taught us anything, it’s that secure digital services are essential for our society to be functional. Mobile devices have become a major part of our daily lives: we buy, we sell, we pay our bills, we communicate with each other, etc. There’s no other place where we hold that much personal and confidential data. No wonder our phones represent a valued target for hackers.
We all expect and deserve security: it is a determining factor in the choice of device and services we make. Long-lasting security and trust are key components of a sustainable business.
QRNG benefits mobile phones manufacturers
Security sells – and Quantum security makes a big difference. With IDQ’s QRNG chip embedded, quantum-level security can be applied to any service and any app on the phone. IDQ’s QRNG chip has been designed and manufactured specifically for mobile handsets, IoT and edge devices. With its low profile, compact size and low power consumption, it is ideal for securing the collection and transfer of sensitive data at the edge. It offers the highest attainable security and robustness for the generation of random bits.
In May 2020, ID Quantique and SK Telecom announced to the world the first 5G smartphone equipped with a Quantum Random Number Generator (QRNG) chipset. By integrating a Quantum Random Number Generator (QRNG) into its new Samsung Galaxy A Quantum smartphone, Samsung has added quantum technology to smartphone security for SK Telecom to provide the highest level of trust for customer’s sensitive information.
This was the world first mass-market application of quantum technology which laid the foundation of affordable high-security key generation into any mobile device. Following this success, Samsung launched the Galaxy Quantum 2 in 2021, the Galaxy Quantum 3 in 2022, and the Galaxy Quantum 4 in 2023 with an expanded use of QRNG to many applications and services in each successive version.


QRNG benefits telecom operators
The QRNG chip adds an additional layer of authentication, boosting security by generating truly unpredictable and random numbers that are used for encryption. This provides smartphone users with a differentiated smartphone service that enables them to use applications and services more securely.
With all of our personal data contained in our smartphones – which are themselves connected to almost everything in our lives – it’s little wonder that security is set to be a major selling point for smartphones and apps. Embedded security hardware offers OEMs and Mobile Network Providers the opportunity to offer the highest level of assurance via a method that is also highly convenient for customers. With the QRNG chip installed in phones, telcos are not only able to differentiate their products and services, but can also enjoy additional revenues from customers who are prepared to pay for enhanced security for their personal data and privacy.
QRNG benefits app developers
Native integration of the QRNG chip into the Android Keystore (APIs) automatically enhances the security of a large number of services used on the smartphone, including mobile payments, banking and identification services, as well as communication and even music streaming services.
All application developers can access the quantum security features for their services with the SDK, making enhanced security more accessible and easier to implement.
Several finance and banking apps are already leveraging QRNG through smartphones equipped with the technology. Among the most notable examples are the partnerships between SK Telecom with DGB Daegu Bank through the quantum-powered banking service IM Bank, as well as with Standard Chartered which is using quantum security through its mobile banking app.
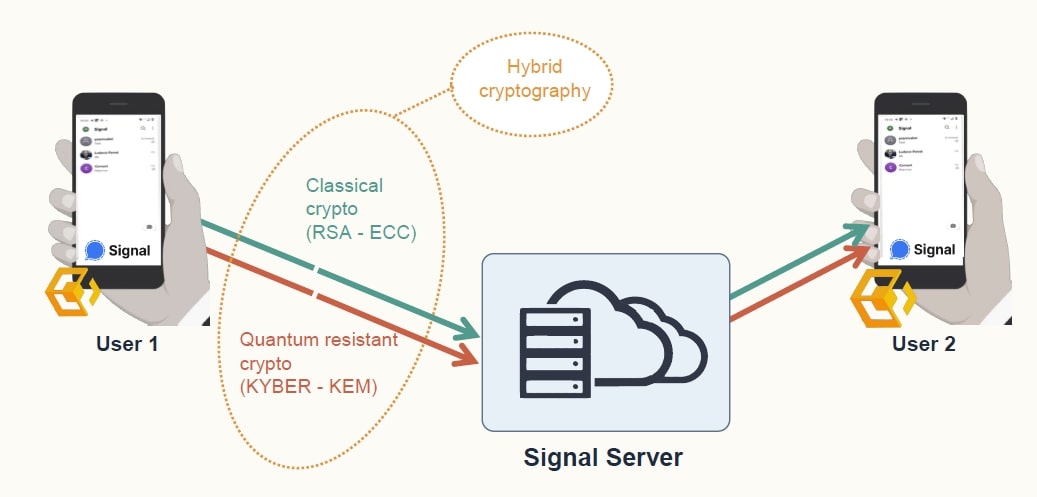
Messaging applications can also be enhanced: CryptoNext has developed a plugin for the Signal application that allows to make Signal quantum resistant. This plugin is an integration of the CryptoNext library with the Signal application. The generation of quantum-resistant cryptographic keys is done on top of Signal and only at the user’s phone level.
The world’s first QRNG chip designed for mobile phone security
Generating strong keys from a reliable entropy source is the cornerstone of any security system.
ID Quantique was the first company to develop a quantum random number generator (QRNG) in 2001 and it remains the market leader in terms of reliability and certifications, with its Quantis QRNG product family. IDQ’s QRNGs offer high quality entropy for use in highly secure crypto operations and solutions requiring proven and certified randomness.
The Quantis QRNG chip:
Our quantum technology provides the most secure encryption keys today and in the quantum computing era, guaranteeing the highest level of trust for consumers.
