The automotive industry has evolved in the past decade: cars have become more connected, smarter, and provide an enhanced driving experience. Since this transformation is driven by advances in computing and communication technologies, the automotive industry must protect itself against a growing and broader threat landscape. Quantum-enhanced security is the go-to technology to secure the basis of any car’s encryption, now and in the long-term future.
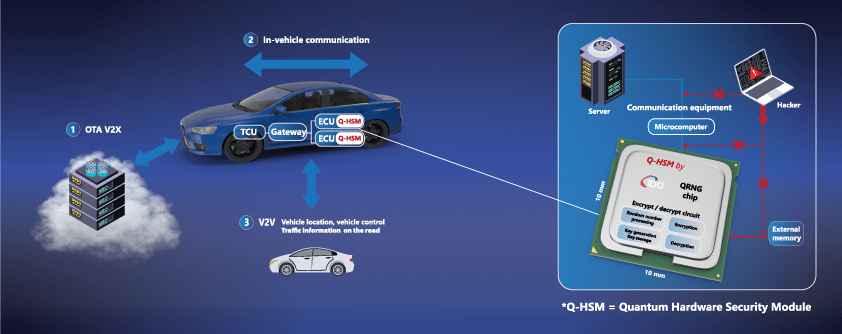
Automobiles have increased the number of in-vehicle systems that use or require over-the-air (OTA) communication to provide the best services to the consumer. The automotive industry is looking to generate new revenues from OTA services, making V2X security a top priority.
Quantum technology enhanced security provides differentiated products with the highest level of trust, while assuring future-proof protection that will resist future technological advancements. It can be embedded reliably in the security system of any connected car to ensure trusted and secured in-vehicle and V2X communications.
The automotive ecosphere and the communications systems connected to the automotive ecosphere are under constant attack. The results are costly and potentially dangerous.
Here are some high profile cyber attacks on some of the largest automotive manufacturers in the world:
It is estimated that cyber-attacks could be performed with the help of quantum computers within the next 5-10 years. As vehicles stay in service typically for more than 10 years, the time for manufacturers to act is now.
From an automotive ecosystem security perspective, vehicle systems, vehicle-to-vehicle networks, vehicle-to-infrastructure networks and back-end systems must be future-proofed by introducing quantum-safe cryptographic solutions as a priority.
IDQ’s range of quantum-safe security solutions are specifically designed to secure data in motion across V2X ecosystems against existing and emerging threats.
Strong key generation is key to ensure a third party cannot guess or deduce the security key. Therefore, the use of truly random numbers is crucial. Quantum Random Number Generation (QRNG) serves this purpose well; instantly strengthening existing cryptographic mechanisms and ensuring new quantum resistant algorithms will remain robust.
IDQ’s Quantis QRNG chip is ideal for integration into automotive HSMs. It provides a clear and robust entropy generation mechanism with a security proof. It is AEC-Q100 certified, with integrated NIST 800-90A/B/C compliant DRBG post-processing.
Features and benefits:
Quantum Key Generation and Quantum Key Distribution are two of the foundation technologies of quantum-safe security. Alongside the evolving use of quantum-safe algorithms, they will form the backbone of the next generation of secure V2X communication networks.
The security of any cryptographic system is determined by the security of its keys. These keys play an integral role in ensuring the confidentiality and integrity of data in motion; alongside the authentication, non-repudiation and access control of the parties involved in the data exchange. For keys to be truly secure, they need to be unique, truly random and stored/distributed securely.
QKD can typically be used to protect data exchange inside the back-end infrastructure, which is a primary target for attackers due to the massive amount of sensitive data that can be stolen at a time.
The combination of QRNG and QKD ensures that keys are generated with high entropy and distributed safely across the network. Vehicular communications are encrypted at a level where they are impervious to both current and ‘hack now, crack later’ attacks, and can be combined with quantum resistant algorithms (QRAs) without major software or hardware upheaval, once they become available.
Murata and ID Quantique have developed a joint cybersecurity integrated circuit (IC) solution based on IDQ’s quantum RNG, and Murata’s HSM technology. It is specifically designed to secure data in motion across V2X ecosystems & in-vehicle against existing and emerging threats, including those posed by quantum computing.

ID Quantique has contributed to the latest SAE EDGE™ Research Report, titled Unsettled Topics Concerning the Impact of Quantum Technologies on Automotive Cybersecurity, which considers a number of unresolved questions around the impact that quantum computing will have on the security of vehicle-to-everything (V2X) ecosystems.